North Korean defectors, journalists who cover North Korea-related news, and entities in South Korea are being zeroed in on by a nation-state-sponsored advanced persistent threat (APT) as part of a new wave of highly-targeted surveillance attacks.
Russian cybersecurity firm Kaspersky attributed the infiltrations to a North Korean hacker group tracked as ScarCruft, also known as APT37, Reaper Group, InkySquid, and Ricochet Chollima.
"The actor utilized three types of malware with similar functionalities: versions implemented in PowerShell, Windows executables and Android applications," the company's Global Research and Analysis Team (GReAT) said in a new report published today. "Although intended for different platforms, they share a similar command and control scheme based on HTTP communication. Therefore, the malware operators can control the whole malware family through one set of command and control scripts."
Likely active since at least 2012, ScarCruft is known for targeting public and private sectors situated in South Korea with an aim to plunder sensitive information stored in the compromised systems, and has been previously observed using a Windows-based backdoor called RokRAT.
The primary initial infection vector used by APT37 is spear-phishing, in which the actor sends an email to a target that is weaponized with a malicious document. In August 2021, the threat actor was unmasked using two exploits in the Internet Explorer web browser to infect victims with a custom implant known as BLUELIGHT by staging a watering hole attack against a South Korean online newspaper.
The case investigated by Kaspersky is both similar and different in some ways. The actor reached out to the victim's associates and acquaintances using stolen Facebook account credentials to establish initial contact, only to follow it up with a spear-phishing email enclosing a password-protected RAR archive that includes a Word document. This decoy document claims to be about "North Korea's latest situation and our national security."
Opening the Microsoft Office document triggers the execution of a macro and the decryption of the next-stage payload embedded within the document. The payload, a Visual Basic Application (VBA), contains a shellcode that, in turn, retrieves from a remote server the final-stage payload with backdoor capabilities.
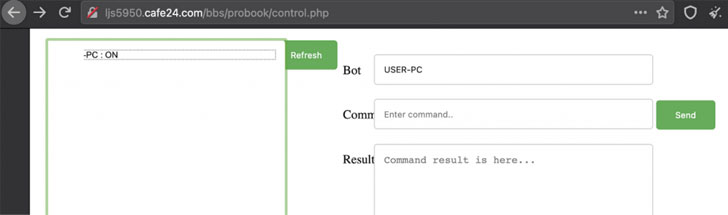
Additional techniques uncovered by GReAT on one of the infected victims show that post its breach on March 22, 2021, the operators managed to collect screenshots for a period of two months between August and September, before deploying a fully-featured malware called Chinotto in late August to control the device and exfiltrate sensitive information to a command-and-control (C2) server.
What's more, Chinotto comes with its own Android variant to achieve the same goal of spying on its users. The malicious APK file, delivered to the recipients via a smishing attack, prompts users to grant it a wide range of permissions during the installation phase, enabling the app to amass contact lists, messages, call logs, device information, audio recordings, and data stored in apps such as Huawei Drive, Tencent WeChat (aka Weixin), and KakaoTalk.
Kaspersky said it worked with South Korea's emergency response teams to take down ScarCruft's attack infrastructure, adding it traced the roots of Chinotto in PoorWeb, a backdoor previously attributed to use by the APT group.
"Many journalists, defectors and human rights activists are targets of sophisticated cyberattacks," the researchers said. "Unlike corporations, these targets typically don't have sufficient tools to protect against and respond to highly skilled surveillance attacks."