Top 10 Vulnerability Management Tools for 2022 – A Complete Review

Despite having more ways than ever to compromise apps, services, and systems, today’s threat actors often opt for the tried and tested path of exploiting vulnerabilities. These vulnerabilities could include out-of-date operating systems, custom apps with code flaws, or database servers with SQL injection vulnerabilities, to name a few. Businesses need a structured vulnerability management program to effectively identify, prioritize, and mitigate the risks presented by vulnerabilities.
Vulnerability management is arguably more challenging than ever as more malicious actors target weaknesses in systems and code—one research report found that the number of new vulnerabilities exploited in the wild rose by 24% during 2021.
Besides, a chronic cybersecurity talent shortage leaves many security teams too stretched to deal with vulnerabilities on time. Tools can play a pivotal role in automating some critical processes in vulnerability management. Read on to learn about the top ten vulnerability management tools for 2022.
The main stages of vulnerability management
Vulnerability management involves five main stages:
- Identifying vulnerabilities—the ability to discover vulnerabilities comes from using various scanners to detect them automatically. Organizations wanting to detect harder-to-find vulnerabilities often enlist the help of penetration testers to probe deeper than scanners.
- Evaluating vulnerabilities—since not all vulnerabilities carry the same level of risk, a pivotal step is evaluating vulnerabilities to determine their potential risk levels. This stage often relies on or gets informed by a standard severity rating, such as The Common Vulnerability Scoring System (CVSS).
- Remediating vulnerabilities—patching is the main way to remediate a vulnerability by removing or fixing the flaw that led to that weakness. Where a patch is not an option, businesses may mitigate the risk in other ways to make the vulnerability less exploitable. Another option is to accept the low-risk vulnerability with little chance of exploitation.
- Verifying vulnerabilities—this stage verifies that remediation actions have eliminated potential threats. Penetration testing can again prove helpful here.
- Reporting vulnerabilities—vulnerability management is an ongoing process that strengthens a company’s future security posture. Improvements come from documenting findings in reports and recommending changes to ensure similar vulnerabilities don’t pose risks in the future. Reporting may also be necessary for compliance purposes.
What is vulnerability management software, and what can it do for me?
Vulnerability management software is essentially a tool or platform that assists with any stage in the vulnerability management process. Some tools try to be all-encompassing and cover much of the management process, while others focus on one or two specific stages.
Some of the tools and features to look out for include:
- Scanners that discover and monitor potential vulnerabilities continuously
- Apps and platforms that display vulnerability severity levels in dashboards and reports along with contextual risk scoring
- The ability to centrally manage software agents or scanners
- Patch management features that help automatically remediate risks
- Customizable reporting based on compliance requirements or business-specific details
- Tools that extend vulnerability identification capabilities to external code and other third-party risks
Top 10 vulnerability management tools for 2022
Here is a round-up of the top 10 vulnerability management tools for 2022, including key features, pros, cons, and prices (where available).
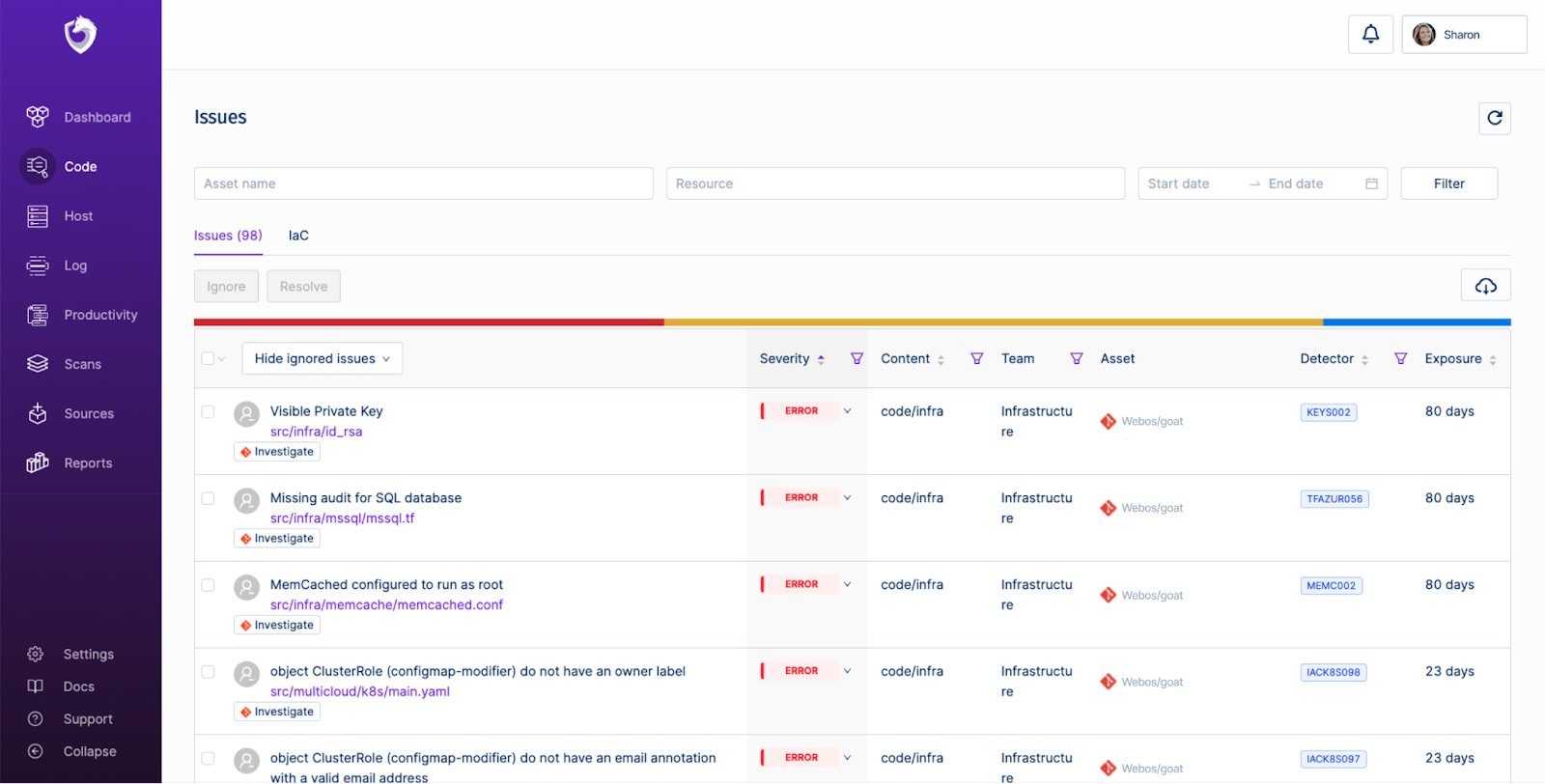
1. Spectral
Key Features:
Spectral is an automated codebase security solution with data loss prevention capabilities. This platform is handy for the identification stage of vulnerability management. You can monitor code, assets, and infrastructure to identify exposed API keys, tokens, credentials, and high-risk security misconfigurations.
Pros:
- Easy to set up and use
- Focuses on developer-first security without the noise that often comes with vulnerability management tools
- Helpful support team
Cons:
- Could do with added options to adjust the order in which issues are presented
Pricing:
Not Disclosed
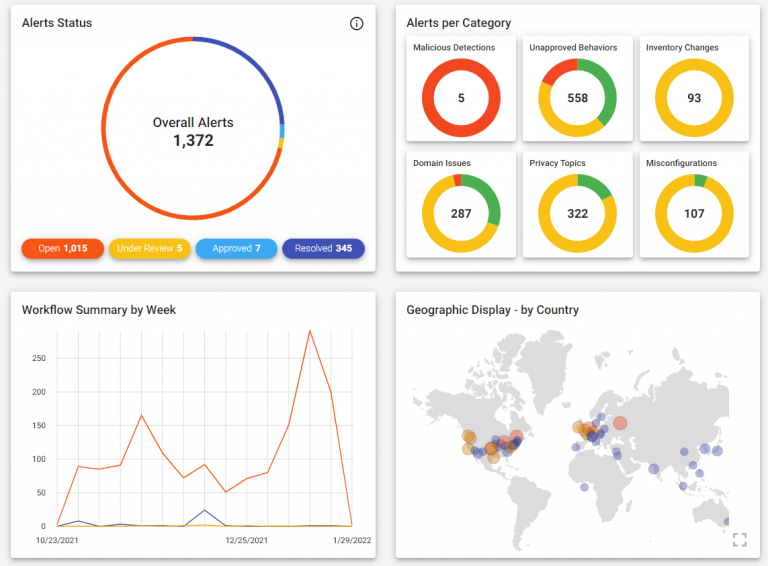
2. Reflectiz
Key Features:
Reflectiz is a unique tool focused on identifying vulnerabilities and monitoring risks from 1st, 3rd, and 4th party risks on client-side applications, such as eCommerce stores and websites. The functionality of modern client-side apps depends heavily on a complex ecosystem of external code, and Reflectiz provides a single pane of glass into this digital supply chain. This is another vulnerability management tool suited for the identification stage of the process.
Pros:
- Simple user interface that makes it easy to understand third-party vulnerabilities and risks in websites
- No work is needed to set the platform up
- Professional and helpful support team
Cons:
- Awaiting implementation for use with Android and iOS apps.
Pricing:
Not Disclosed
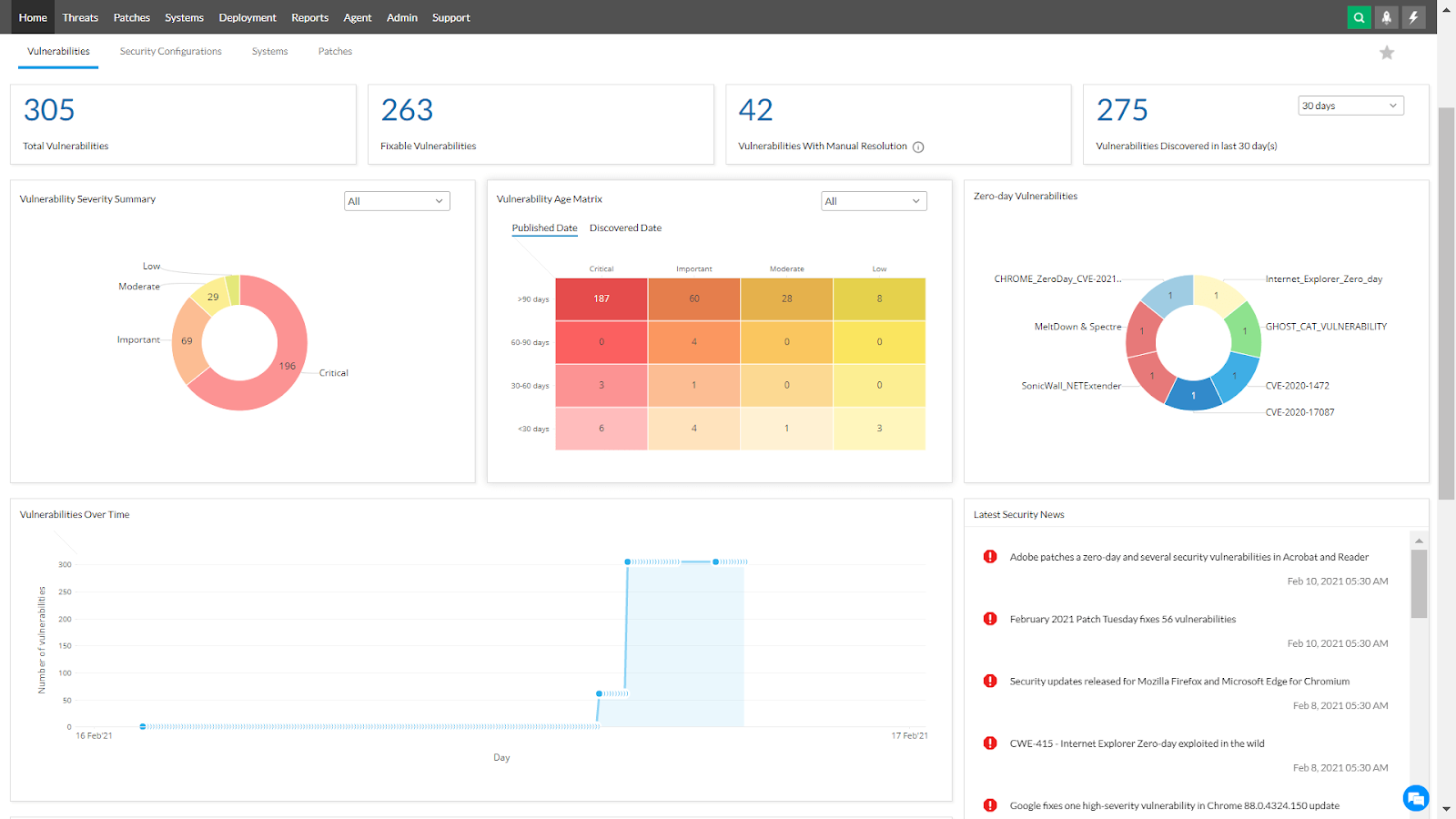
3. ManageEngine Vulnerability Manager Plus
Key Features:
This enterprise vulnerability management solution aims to provide 360-degree insight into companies’ security exposures, focusing on vulnerabilities, misconfigurations, and high-risk software. Features include vulnerability assessments, patch management, and zero-day mitigation. ManageEngine is suitable for vulnerability management’s identification, evaluation, and mitigation stages.
Pros:
- User-friendly features and easy to use
- Product is regularly improved based on customer feedback
Cons:
- Reports aren’t quite up to scratch
Pricing:
The Professional edition (usable on 100 workstations) costs $695 per month.
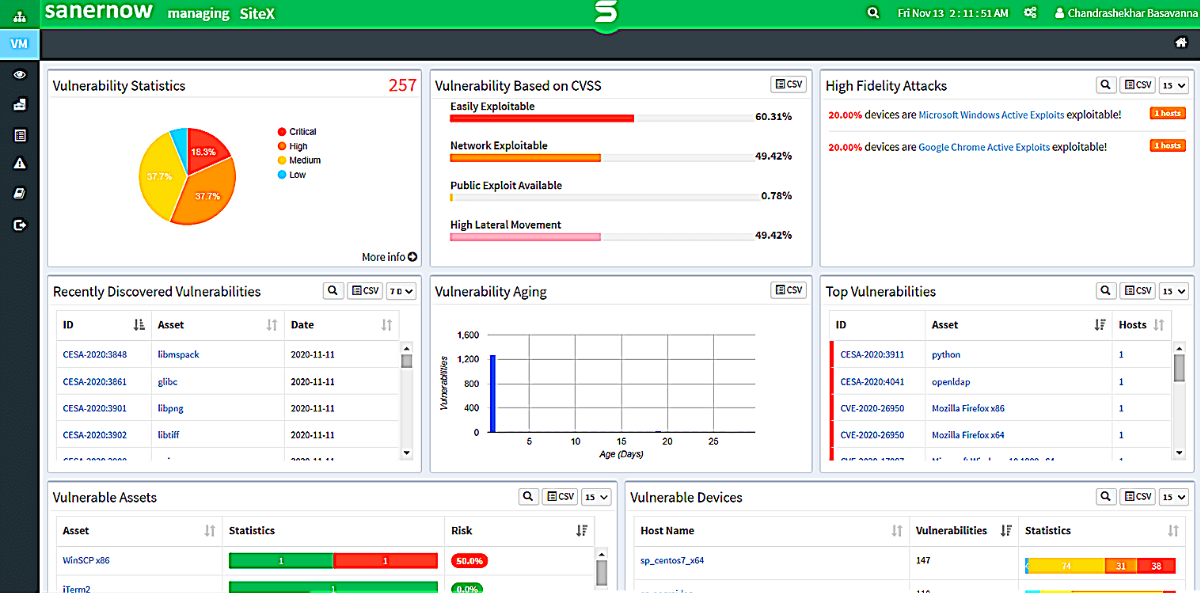
4. SanerNow Vulnerability Management
Key Features:
SanerNow has a built-in vulnerability database with 160,000+ software vulnerability checks. The engine uses smart and lightweight agents that you can deploy across endpoints to monitor, manage, and remediate any software vulnerability. Also, coming with integrated patch management, you can use SanerNow for vulnerability management’s identification, evaluation, and mitigation stages.
Pros:
- Works on multiple operating systems (Win, macOS, Linux)
- Comprehensive vulnerability scans that run quickly
Cons:
- Could improved admin dashboards and compliance management features
Pricing:
The starting price is $50 per year per device
5. Italik Vulnerability Management as a Service
Key Features:
Italik’s offering is a service-based option that scans for and identifies vulnerabilities in your IT environment. The results are then presented to your security team on a single platform, along with reports prioritizing vulnerable assets by severity. You could use this service-based option to handle vulnerability management’s identification and evaluation stages. Your security team will need to take remediation, verification, and reporting actions.
Pros:
- Removes much of the ongoing burden from vulnerability management
- The service structure is scalable so that it easily adapts to changes in your business
Cons:
- Several significant sources of vulnerabilities are only scannable for an optional extra monthly fee (e.g., network perimeter or web apps)
Pricing:
Costs vary depending on the number of employees (for internal scans) and the number of devices for external scans. A company with 51-100 employees pays £270.00 (GBP) per month for internal scans. Scanning 14 external devices costs £125.00 per month.
6. Flashpoint Vulnerability Management
Key Features:
FlashPoint focuses on vulnerability identification and remediation. The solution uses a comprehensive vulnerability database that provides findings and insights beyond typical common vulnerability exposures (CVEs). Vulnerabilities are also presented with extra metadata, including exploit details and attack vectors.
Pros:
- It comes with automation capabilities for accelerating repeatable vulnerability management processes
- A user-friendly platform makes it easy for analysts to understand and process vulnerability data
Cons:
- Customer support can be slow or even unresponsive at times
Pricing:
Not disclosed
7. Tripwire Vulnerability Management Platform
Key Features:
Tripwire’s vulnerability management suite provides a complete view of your vulnerability profile across IT and OT devices and software. The platform contains multiple solutions, including IP360, which uses an application-centric approach to vulnerability scanning. Other solutions focus on vulnerability visibility in industrial control system environments or DevOps pipelines.
Pros:
- Smooth deployment and easy to integrate across an IT environment
- Comprehensive database for scanning and identifying vulnerabilities
Cons:
- Vulnerability scans seem to notably impact the performance of any machines on which they run
Pricing:
Not Disclosed
8. Invicti
Key Features:
Invicti is a useful tool for vulnerability management’s identification and verification stages. Invicti works on web applications and can be integrated into software development lifecycles. It uses a proof-based approach to automatically exploit detected vulnerabilities (in a safe way) so that you know you’re not seeing false positives.
Pros:
- Simplifies vulnerability management with accurate identification and verification so that security teams always mitigate exploitable vulnerabilities
- The user interface is intuitive, and support staff are responsive
Cons:
- Scans can sometimes run slowly
Pricing:
Not Disclosed
9. FirstPoint
Key Features:
FirstPoint is a somewhat different vulnerability management tool in that it’s actually a connectivity management platform for IoT (Internet of Things) devices. In practice, you can use FirstPoint to detect, alert, and block vulnerabilities in IoT devices. As more businesses adopt IoT, threat actors will increasingly target these sensors, actuators, and other smart devices.
Pros:
- Expands your vulnerability management capabilities to cover IoT devices
Cons:
- Limited to vulnerability management in businesses that have connected IoT devices
Pricing:
Not disclosed
10. OWASP Zed Attack Proxy (ZAP)
Key Features:
This open-source web application security scanner is designed for a number of software security testing methods, including penetration tests, vulnerability assessments, runtime tests, and code reviews. The vulnerability assessment features help businesses identify vulnerabilities by automatically scanning applications.
Pros:
- Scans run quickly
- Works across all main operating systems
Cons:
- Slightly outdate UI.
Pricing:
Free
Understand what’s happening behind the scenes
Effective vulnerability management tools help you better understand what’s really happening behind the scenes in your IT environment and where the most concerning points of potential exploitation are. In deterring and defending against today’s complex cyber threats, it’s not enough just to highlight the risks lurking in your assets. Getting visibility over a growing inventory of third-party applications is more important than ever, as websites and apps rely on this external code to power their features and functions. Learn more about the must-haves for modern vulnerability assessments here.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!